

e-Biz Impact security allows you to define role-based authorization for command and control (CNC) requests that are executed using the Global Console, the CNC command line utility, and the Java remote.CncProxy.
To implement e-Biz Impact security, you set up Data Source Names (DSNs) that represent ODBC database connections for the Authorization Console and each cluster in your environment. These connections allow the authorization client (Authorization Console) and the e-Biz Impact server-hosted cluster to communicate with the authorization database.
Once you have created the DSNs, you use the Authorization Console to define roles that you associate with objects and groups. This builds a security policy that authorizes a role to execute commands defined in the group against the selected object. When you create a user and assign that user a role, they are authorized to execute the commands on the object associated with that role.
Figure 1-1: Setting up security in the Authorization Console
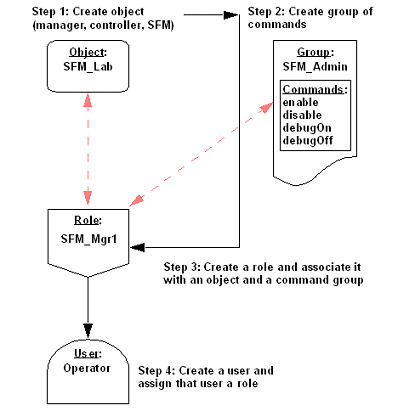
For example, Figure 1-1 illustrates how you can create the SFM_Lab object, then associate that object with the SFM Administration group of commands. You create the SFM_Mgr1 role, then assign the Operator user that role. Because the Operator user has the SFM_Mgr1 role, they are authorized to perform the SFM Administration commands on the SFM_Lab1 object.
If you choose not to use e-Biz Impact security:
You do not have to run the authorization database to use the Global Console.
All users can execute all commands from the Global Console, from the CNC command line utility, and with the Java remote.CncProxy.
| Copyright © 2005. Sybase Inc. All rights reserved. |

|
|