

Once you establish a connection in the Authorization Console, the tree view (left pane) displays modules in use by cluster security—Administrators, Users, Object Types, Roles, Objects, Commands, and Groups. Each module represents a table in the authorization database.
Figure 3-1: Authorization Console
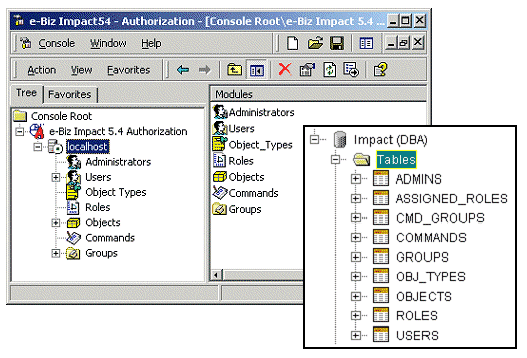
When you select module in the tree view, the right pane displays the individual objects within that module.
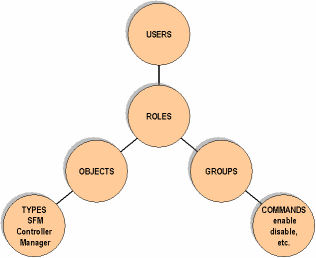
The rest of this chapter describes how to configure the authorization components. The relationship of these components to one another is illustrated in Figure 3-2.
Figure 3-2: Authorization architecture
To configure security, follow these steps:
Set up the administrator user that creates the security policy for the e-Biz Impact implementation. See “Setting up administrators”.
Define the objects upon which you want to implement security. See “Defining objects”.
Create groups and add commands to the groups. See “Defining groups” and “Adding commands to a group”.
Define roles and associate each role with an object and a group. Users that are assigned a role have permission to execute the commands associated with that role’s group and object. See “Defining roles”.
Create users and assign them roles. See “Defining users”.
| Copyright © 2005. Sybase Inc. All rights reserved. |

|
|