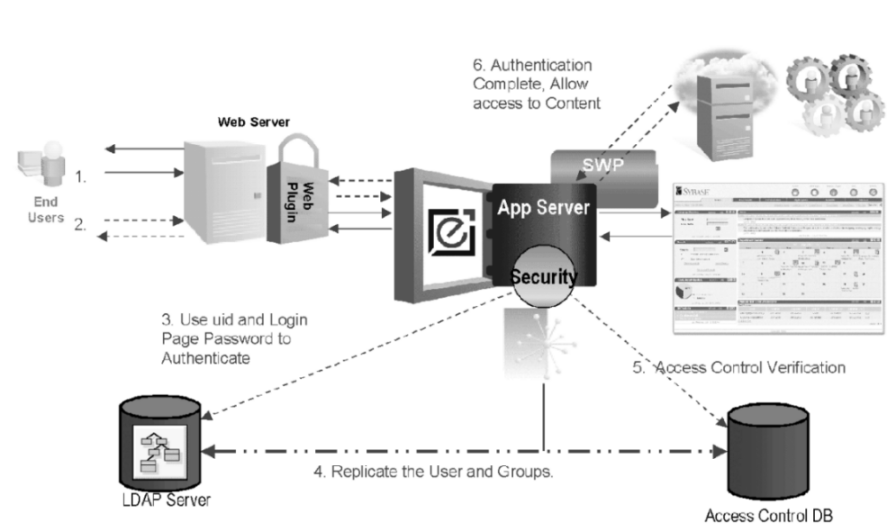
Generally, the most commonly implemented form of protecting resources is verifying the identity of the person trying to enter the network system—authentication. Enterprise Security supports two types of user authentication—user name and password, and digital certificates.
Figure 1-1 illustrates the authentication process, where:
A user accesses the portal login page through a Web browser.
The user enters his or her user name and password.
An authentication request with the user name and password is passed to either an LDAP server or the ACDB.
If authentication is performed through LDAP, the information (success or failure) is replicated to the ACDB.
The system verifies that the user has permission to read the home page.
The user is authenticated and the home page displays.
Figure 1-1: Enterprise system architecture